Charities need to prioritize their cybersecurity measures. It’s no longer a matter of if, but when, a cyber attack will occur. This extensive guide outlines the essential steps charities can take to enhance their cybersecurity and protect their valuable data.
Understanding Cybersecurity Risks for Charities
Charities, like all organizations, are at risk of cyber attacks. These attacks can have severe consequences, including data leakage, financial loss, and damage to the charity’s reputation. Understanding these risks is the first step toward effective protection.
– The Reality of Cyber Threats:
Cyber threats are a reality for all organizations, including charities. With the rise of sophisticated cyber attacks, no organization can confidently say they will not be targeted. The aim is to make it as challenging as possible for cybercriminals to penetrate the charity’s defenses.
– The Importance of Cybersecurity in Charities:
The importance of cybersecurity in charities cannot be overstated. Charities hold sensitive data like donor information, employee details, and financial records. A cyber breach could lead to the loss or exposure of this data, damaging the trust of donors, employees, and beneficiaries.
Initial Cybersecurity Measures for Charities
Implementing initial cybersecurity measures can greatly reduce a charity’s vulnerability to attacks. These measures should focus on both end users and the charity’s IT infrastructure.
– Password Policies:
Establishing or revising a company password policy is a crucial first step. Passwords should be required on all devices employees use. They should be changed regularly, and employees should not be allowed to reuse old passwords. Furthermore, consider using multi-factor authentication (MFA) for an added layer of security.
– Cybersecurity Training
Training end users to be aware of various threats is a longer-term effort that can pay dividends. This includes being suspicious of emails requesting credential confirmation, checking website security before visiting, and ensuring sensitive information is transmitted securely.
– Limiting Access
Not all employees need access to all aspects of the charity’s operations. It’s essential to emphasize that limiting access is a critical part of protecting the charity against cyber attacks.
IT Infrastructure-Focused Measures
Charities also need to take measures focused on their IT infrastructure. These actions can further strengthen the charity’s defenses against cyber threats.
– Installing Protection
Installing additional protection, such as firewalls and antivirus software, can help shield the charity’s IT infrastructure against cyber attacks. Regularly updating and patching all software is also essential.
– Backing Up Files
Backing up files is another immediate action charities should take. This can be done offline, using external hard drives, or by backing up to the cloud. Furthermore, encrypting backups can provide an extra layer of security.
– Implementing Security Tools
Implementing security tools like browser management, DNS filtering, network monitoring, and endpoint protection can help detect and prevent cyber attacks.
External Resources for Cybersecurity Guidance
There are many external resources available to help charities improve their cybersecurity. These include government agencies, nonprofit organizations, and specific groups associated with nonprofit verticals.
– Government Agencies
Government agencies like the U.S. Department of Homeland Security Cybersecurity & Infrastructure Security Agency (CISA), the Federal Trade Commission, and the National Institute of Standards and Technology (NIST) offer resources on cybersecurity.
– Nonprofit Organizations
Nonprofit organizations like the Cyber Readiness Institute, Global Cyber Alliance, and the National Council of Nonprofits also offer resources to help charities improve their cybersecurity.
Following the NIST Cybersecurity Framework
The National Institute of Standards and Technology (NIST) has developed a five-part best practices framework to help firms focus resources for cybersecurity protection. These steps include identifying, protecting, detecting, responding, and recovering from cyber attacks. The NIST framework offers a systematic approach to managing cybersecurity risks. It includes identifying all equipment, software, and data used; protecting data with security software and regular backups; detecting unauthorized access; responding effectively to attacks; and recovering after an attack.
Implementing Advanced Cybersecurity Measures
Implementing advanced cybersecurity measures can provide an additional layer of protection for charities. These measures include identity and access management (IAM), securing networks, and moving to the cloud.
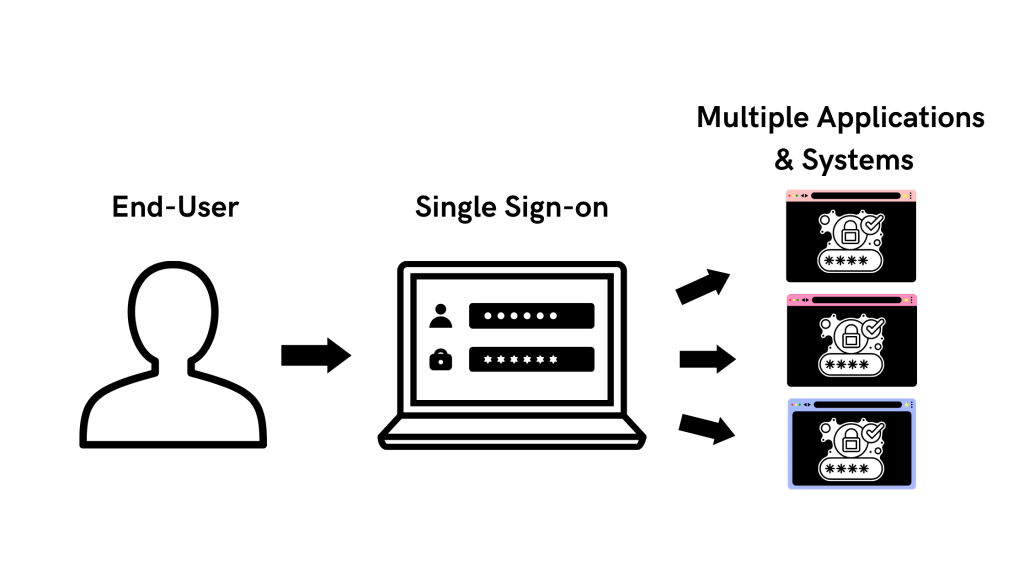
– Implementing IAM
Implementing IAM can streamline access for users internally and externally. Features like single sign-on (SSO), social sign-on, and multi-factor authentication (MFA) can make it easier for authorized users to access the charity’s websites and applications.
– Securing Networks
Securing networks business class equipment from trusted brands can boost a charity’s network security. This includes using wired and wireless networking hardware to create a functioning network and protecting against online threats.
– Moving to the Cloud
Moving to the cloud can provide charities with flexibility and resilience. Cloud-hosted systems allow for secure work from anywhere and can help charities bounce back faster after a cyber attack.
Preparing for Cyber Attack Recovery
Preparing for cyber attack recovery is crucial. When defenses fail, charities need the ability to bounce back quickly.
– Data Backup and Restoration
Data backup and restoration is a key part of cyber attack recovery. Charities should regularly back up their data to protect against data-loss disasters. If an attack occurs, they can restore their data and resume operations quickly.
– Developing a Continuity of Operations Plan
Developing a continuity of operations plan can ensure that a charity can continue to serve its community even when disaster strikes. This includes planning for how to keep business operations up and running and reporting the attack to law enforcement and other authorities.
Contact us today to explore how to best setup your cybersecurity efforts, ensuring protection and compliance in an ever-evolving cybersecurity landscape.