God has recently lead me to do some charity volunteer work for a worldwide organization and their IT department. My first project was to untangle their Nagios Core system and then take over the administration of that server and the monitoring of the rest of the network. Part of this volunteer work took place yesterday with deep dive into the Nagios framework, Linux and SNMP to allow monitoring APC UPS devices.
Initial Trip Off Course
My initial thought was not to re-invent the wheel and head to the Nagios Exchange to find a pre-made project that would elegantly provide monitoring APC UPS devices. I found the check_apcupsd project which looked simple and had a great screenshot. Little did I know what I was getting into. Turns out there are a couple undocumented dependencies for this including apcupsd itself and an undocumented connection to port 3551 which I could not find inside the portal page for the SMART-UPS 1500 network management card. After a couple hours of frustration I abandoned this and removed all linux packages associated with it.
Trip Down SNMP lane
After looking over other projects at the Nagios Exchange, I decided to research using SNMP to provide monitoring APC UPS devices. This lead me to an article by Mihai Radoveanu which provided the detailed steps to create monitoring APC UPS devices in Nagios Core. He details editing the command.cfg file to add the check_snmp and his own check_snmp_inverter to list of commands. (Please note that the check_snmp_inverter.sh file will need to be edited to Change the Home variable to point to the Nagios Core plugins directory) He details creating host templates, host groups, adding a separate configuration file to the main file which includes hosts and services. I prefer the more standards based approach to creating individual host files, adding them to a host group and then creating a service file that points to the host group. Made these changes to the Nagios Core framework and confirmed my configuration before making the changes live.
APC Changes Needed
Finally came the changes to the APC UPS network management card configuration:
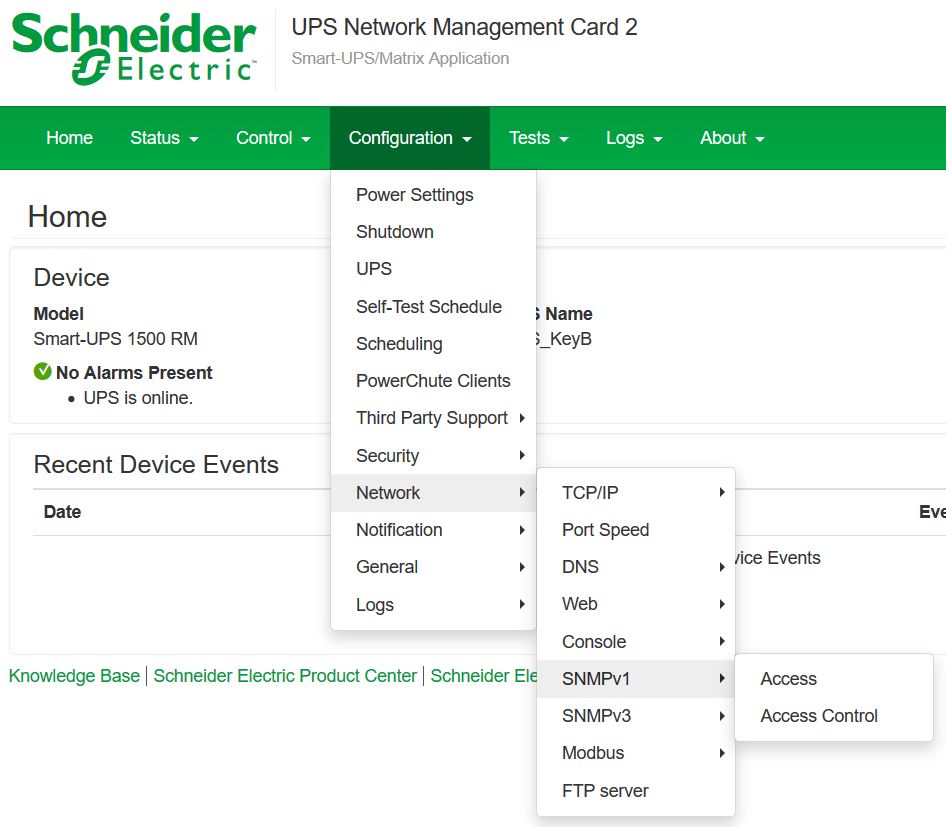
- Login to the network management card webpage, click on Configuration > Network > SNMPv1 > Access then check the box next to Enable and click on Apply.
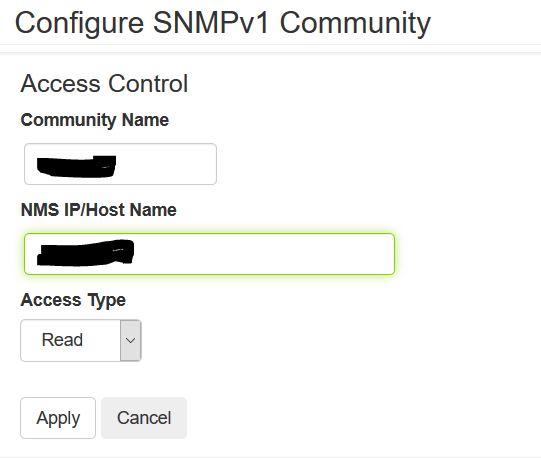
- Click on Configuration > Network > SNMPv1 > Access Control then click on a community name then type in the network SNMP community name and the IP address of the Nagios Core server. It will only need Read permissions. Click on Apply.
That is all that is needed. This introduction to the Nagios Core framework later allowed me to setup SNMP monitoring for the High Availability link ports between their Sonicwall 4600 devices.
If you are looking for expert monitoring of your network systems by highly trained technicians, then contact us for assistance.