Recently have had to setup a couple terminal servers and wanted to create a list of standard lock downs that can be added via a Terminal Server lockdown Group Policy Object (GPO).
Terminal Server Lockdown Preparation
1. Open Active Directory Users & Computers
2. Create Organizational Unit (OU) for Terminal Server.
3. Move all terminal servers to this OU.
4. Create Security Group in this OU for users who will use Remote Desktop Host (i.e. Terminal Server Users).
5. Add all users who will use the terminal server as members of this security group. 6. Open Group Policy Management, right click the new Terminal Server OU and “Create a GPO in this domain, and Link it here” (i.e. Terminal Server Lock Down).
7. In Security Filtering delete Authenticated Users, add Terminal Server Users security group created in previous step.
Configure users who can connect to the server remotely:
1. Log into the terminal Server
2. Open Control Panel, open System, click on Remote Settings then click on the Remote tab.
3. Click on Select Users, Remove any groups/users and then Add the Terminal Server Users security group.
Disable Server Manager Pop Up at user log on:
1. On Terminal Server open Task Scheduler.
2. Navigate to Task Scheduler Library\Microsoft\Windows\Server Manager.
3. Disable task “ServerManager” which triggers at log on of any user.
Configure Group Policy for Terminal Server Lock Down:
Loopback Processing:
[Computer Configuration\Policies\Administrative Templates\System\Group Policy]
Configure user Group Policy loopback processing mode: Enable – Merge
Disable Control Panel Items:
[User Configuration\Policies\Administrative Templates\Control Panel]
Hide specified Control Panel items: Enable
Add following items to the disallowed Control Panel items:
Microsoft.AdministrativeTools
Microsoft.AutoPlay
Microsoft.ActionCenter
Microsoft.ColorManagement
Microsoft.DefaultPrograms
Microsoft.DeviceManager
Microsoft.EaseOfAccessCenter
Microsoft.FolderOptions
Microsoft.iSCSIInitiator
Microsoft.NetworkAndSharingCenter
Microsoft.NotificationAreaIcons
Microsoft.PhoneAndModem
Microsoft.PowerOptions
Microsoft.ProgramsAndFeatures
Microsoft.System
Microsoft.TextToSpeech
Microsoft.UserAccounts
Microsoft.WindowsFirewall
Microsoft.WindowsUpdate
Microsoft.DateAndTime
Microsoft.RegionAndLanguage
Microsoft.RemoteAppAndDesktopConnections
Install Application On Remote Desktop Server
Java
Flash Player
Remove Administrative Tools and Powershell:
Restrict access to Administrative tools:
1. Navigate to:
[Computer Configuration\Policies\Windows Settings\Security Settings]
2. Right click on File System, choose Add File… .
3. In the Add a file or folder window, type the following in the Folder field and click OK:
%AllUsersProfile%\Microsoft\Windows\Start Menu\Programs\Administrative Tools

4. On the next window, Database Security, remove Users and check that Administrators have Full Access.
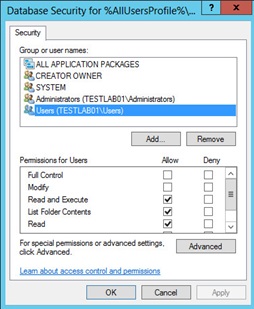
5. On the Add Object window choose Configure this file or folder then Propagate inheritable permissions to all subfolders and files then click OK.
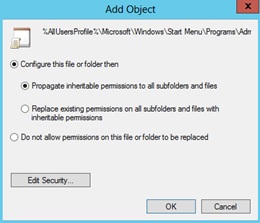
6. Repeat the above steps for the PowerShell shortcut (in addition delete Creator Owner in database security):
%AllUsersProfile%\Microsoft\Windows\Start Menu\Programs\System Tools\Windows PowerShell.lnk
7. Repeat the above steps for the Server Manager shortcut:
%AllUsersProfile%\Microsoft\Windows\Start Menu\Programs\Administrative Tools\Server Manager.lnk
File Explorer Configuration:
[User Configuration\Policies\Administrative Templates\Windows Components\File Explorer]
Enable – Restrict A, B, C and D drives only: Hide these specified drives in My Computer
Enable – Remove Hardware tab
Enable – Hides the Manage item on the File Explorer context menu
Enable – Remove Security tab
Disable Registry Modification:
[User Configuration\Policies\Administrative Templates\System]
Enable – Prevent access to registry editing tools
Configure Windows Installer and Windows Updates:
[Computer Configuration\Policies\Administrative Templates\Windows Components\Windows Installer]
Enable: Prevent users from using Windows Installer to install updates and upgrades
Enable Always: Turn off Windows Installer
[Computer Configuration\Administrative Templates\Windows Components\Windows Update]
Enable: Do not display ‘Install Updates and Shut Down’ option
[Computer Configuration\Administrative Templates\Windows Components\Windows Update]
Enable: Do not display ‘Install Updates and Shut Down’ option
Disable: Allow non-administrators to receive update notifications
Additional Policies:
[Computer Configuration\Policies\Administrative Templates\Windows Components\Remote Desktop Services\Remote Desktop Session Host\Session Time Limits]
Enable (i.e. 30 minutes): Set time limit for disconnected sessions
[Computer Configuration/Policies/Administrative Templates/Windows Components/Remote Desktop Services/Remote Desktop Connection/Remote Desktop Session Host/Session Time Limits]
Set time limit for logoff of RemoteApp sessions: Enable (i.e. logoff delay 1 hour)
[Computer Configuration/Policies/Administrative Templates/Windows Components/Remote Desktop Services/Remote Desktop Connection/Remote Desktop Session Host/Session Time Limits]
Set time limit for active but idle Remote Desktop Services sessions: Enable ( i.e. 1 hour)
[User Configuration/Policies/Administrative Templates/Start Menu and Taskbar]
Go to the desktop instead of Start when signing in or when all the apps on a screen are closed: Enable
[User Configuration/Policies/Administrative Templates/Start Menu and Taskbar]
Remove the Action Center icon: Enable
[User Configuration/Policies/Administrative Templates/Windows Components/Windows Update]
Remove access to use all Windows Update features: Enable (0 = Do not show any notifications)
[User Configuration/Policies/Administrative Templates/Windows Components/File Explorer]
Remove CD Burning features: Enable
[User Configuration/Policies/Administrative Templates/Windows Components/File Explorer]
Prevent access to drives from My Computer: Enable (choose the drives)
[User Configuration/Policies/Administrative Templates/Windows Components/Credentials User Interface]
Do not display the password reveal button: Enable
[User Configuration/Policies/Administrative Templates/Windows Components/AutoPlay Policies]
Turn off Autoplay: Enable (CD-ROM and removable media drives)
[User Configuration/Policies/Administrative Templates/Windows Components/Remote Desktop Services/Remote Desktop Connection]
Do not allow passwords to be saved: Enable
For detailed explanations of what each of these items does please see the notes in each individual Group Policy setting.



THANK YOU.
I was looking for something like this for a 2016 TS server.
I added some in the start and taks bar but thats just personal taste
Thank you again
Do these policies apply equally well to a 2019 TS server? I’m assuming they do since 2016 and 2019 aren’t that different, but it would be good to have confirmation.
Thanks!
Same policies apply. I haven’t dug deep to see what new policies are available in 2019. Maybe I should and update this post.
Note sure about new policies – it’s very complex! Also, it’s very hard to find some of the policies already mentioned above, because different versions of the ADMX files have different names for some items. In the versions that I’m using (probably all Windows 2016 and above):
“Remove the Action Center” is now named “Remove Notifications and Action Center”
“Remove access to use all Windows Update features” is now named “Remove links and access to Windows Update”
Thanks for this article!
I have tried this and can’t get the loop back to work. I have tried all variations
What version of Windows Server are you using?
I got the loopback working on server 2019
you need to keep authenticated users, filtering does not work here.
then under delegation add your admin user or group and select advanced followed by “deny” apply policy.
Thank you Peter, this had me scratching my head for a few minutes.