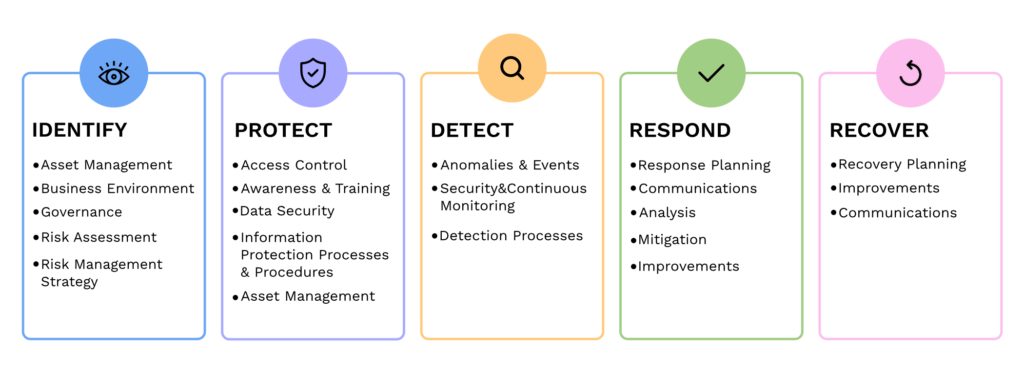
It has become increasingly crucial for businesses to prioritize cybersecurity. We all need to be proactive in safeguarding sensitive information and protecting against cyber threats. The National Institute of Standards and Technology (NIST) has been providing standards for cybersecurity practices. We will now delve into the updates and key changes in the fourth revision of the renowned NIST 800-53 publication.
- Expanded Scope:
NIST 800-53 Revision 4 broadens the standards scope to include private sector organizations dealing with sensitive information. This expansion reflects the need for all companies to implement cybersecurity best practices.
- Threats and Vulnerabilities:
This revision incorporates emerging threats and vulnerabilities faced by organizations today, such as advanced persistent threats, insider threats, supply chain risks, and cloud computing challenges. It emphasizes the importance of a comprehensive approach to identify and mitigate these risks effectively.
- Security and Privacy:
NIST 800-53 Revision 4 highlights the connection between security and privacy. The guidelines provided help organizations maintain the delicate balance of ensuring data protection while respecting privacy rights.
- Continuous Monitoring and Assessment:
One significant change is the emphasis on continuous monitoring. Instead of periodic assessments, companies are urged to implement an ongoing, systematic approach to monitor security, identify vulnerabilities, and respond to them in real-time. This proactive approach helps in detecting and mitigating threats promptly.
- Role-Based Access Controls (RBAC):
Another notable addition is the strengthening of Role-Based Access Controls (RBAC). This approach ensures that users only have access to the information and functions that are needed to complete their jobs. Implementing effective RBAC helps minimize the risk of unauthorized access, privilege escalation, and data breaches.
- Supply Chain Risk Management (SCRM):
Revision 4 also emphasizes the need for proper Supply Chain Risk Management (SCRM) practices. It recommends involving suppliers and stakeholders in security assessments and due diligence processes to mitigate risks associated with third party software, hardware, and services.
Remember, cybersecurity is a journey, not a one-time event. Stay vigilant, adapt to evolving threats, and contact us to create a comprehensive cybersecurity strategy to safeguard your business assets and reputation.