Had another tech firm that needed some Tier 3 assistance as they were having trouble with their VPN connection. I helped them setup Azure to Unifi USG IPSec VPN to connect their headquarters to the hosted RemoteApps server. This tutorial will go into detail about the creation of this tunnel starting with the Microsoft Azure side first using Resource Manager. It will be using the following parameters:
- VNet Name: TestNetwork
- Address Space: 10.10.0.0/16
- Subnets:
- Primary: 10.10.10.0/24
- GatewaySubnet: 10.10.0.0/24
- Resource Group: TestResourceGroup
- Location: West US
- DNS Server: Azure Default
- Gateway Name: TestVPNGateway
- Public IP: TestVPNGatewayIP
- VPN Type: Route-based
- Connection Type: Site-to-site (IPsec)
- Gateway Type: VPN
- Local Network Gateway Name: TestSite
- Local Subnet: 10.20.20.0/24
- Connection Name: VPNtoTestSite
Configure an Azure VPN gateway
This part takes the longest, so it should be done first:
- Click on the “+” icon at the top left hand side of the Resource Manager, then search for “Virtual Network Gateway” and click on the “Create” button.
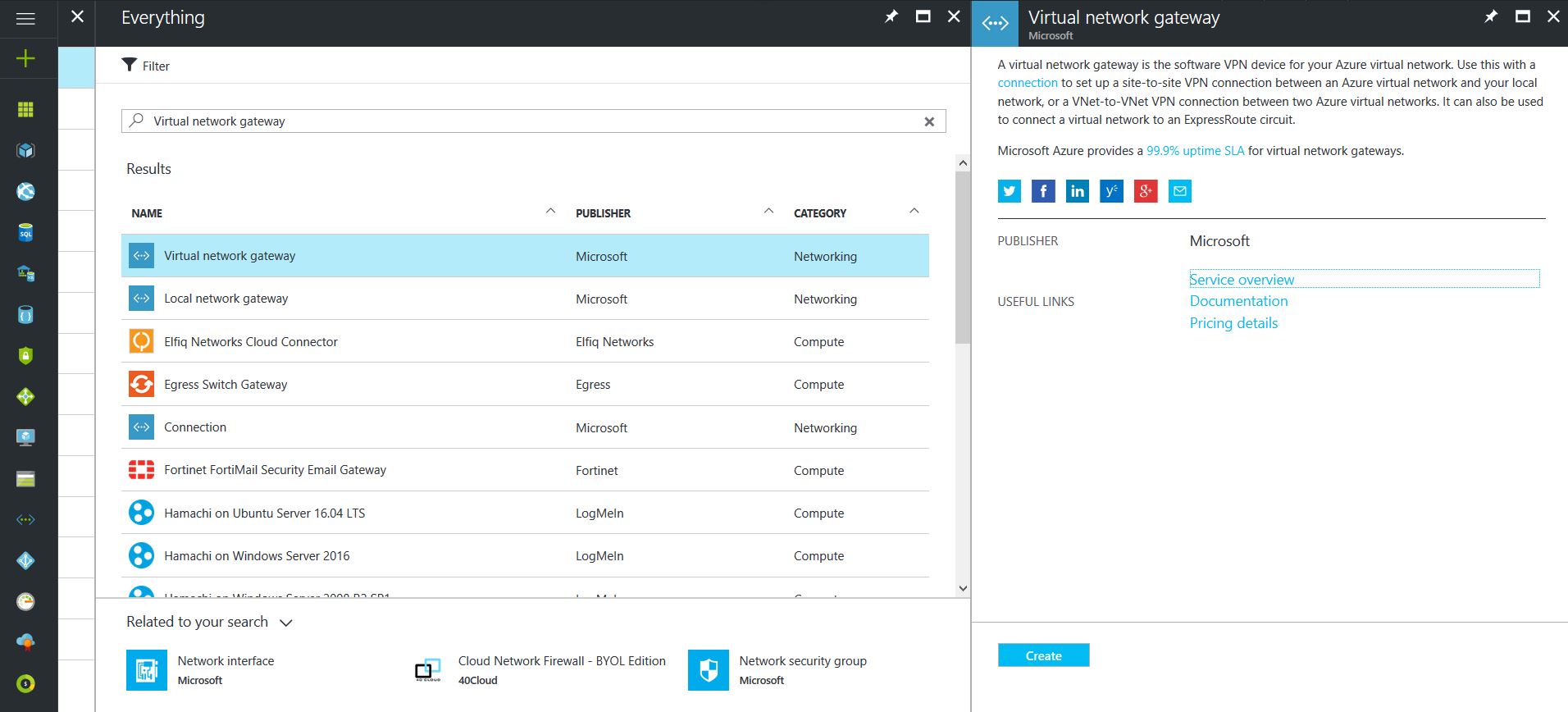
- Give the Virtual Network Gateway a name
- Select matching Region to where Azure resources are located
- Leave Gateway & VPN type the defaults
- Choose a SKU <- These have changed since the article was created, so my “standard” now is WpnGw1 with Active / Active turned off (this is a good balance of performance and cost)
- Choose or create a local network (not covered here) that matches internal resources
- Choose or create a Public IP Address
- Leave the remaining values as their defaults and then click the “Create” button. (Please note the reminder that this takes 45 minutes to create!)
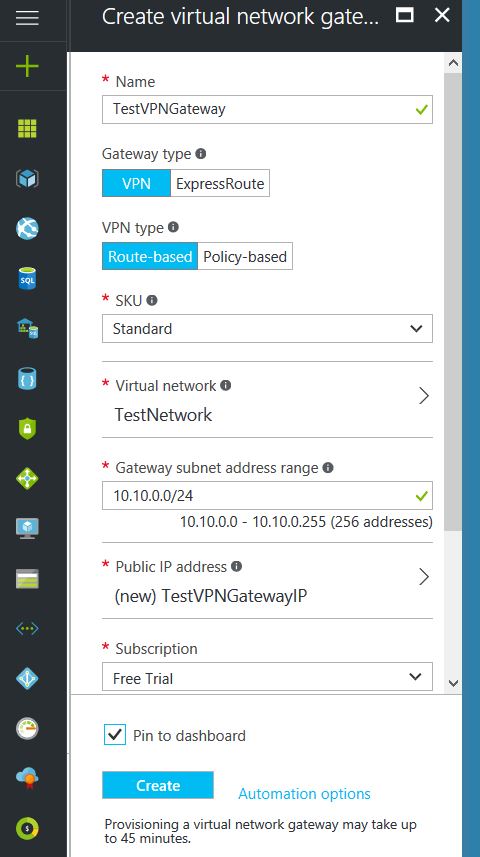
Configure an Azure Local Network Gateway
This is a reference to your on-premise network so that subnets can pass traffic:
- Click on the “+” icon at the top left hand side of the Resource Manager, then search for “Local Network Gateway” and click on the “Create” button.
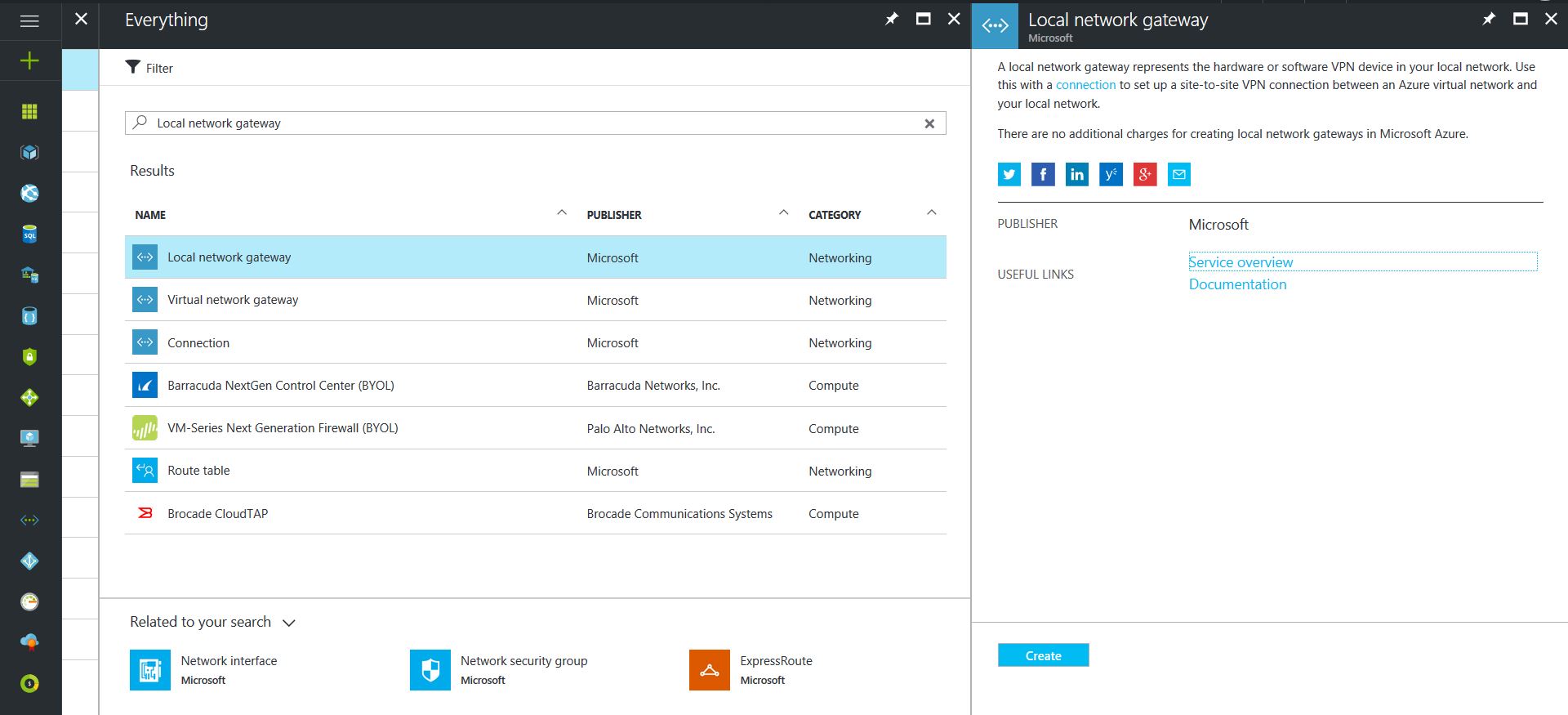
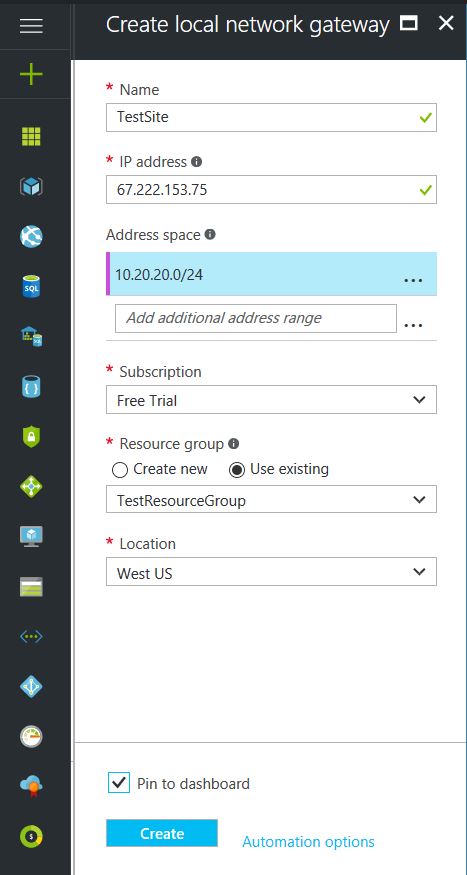
- Give the Local Network Gateway a name
- Select matching Region to where Azure resources are located
- Specify the external IP address of the local on-premise site
- Specify the on-premise address space (subnet)
- Leave the remaining values as their defaults and then click the “Create” button.
Configure an Azure VPN Connection
This will create the tunnel from Azure to the on-premise site:
- Click on the “+” icon at the top left hand side of the Resource Manager, then search for “Connection” and click on the “Create” button.
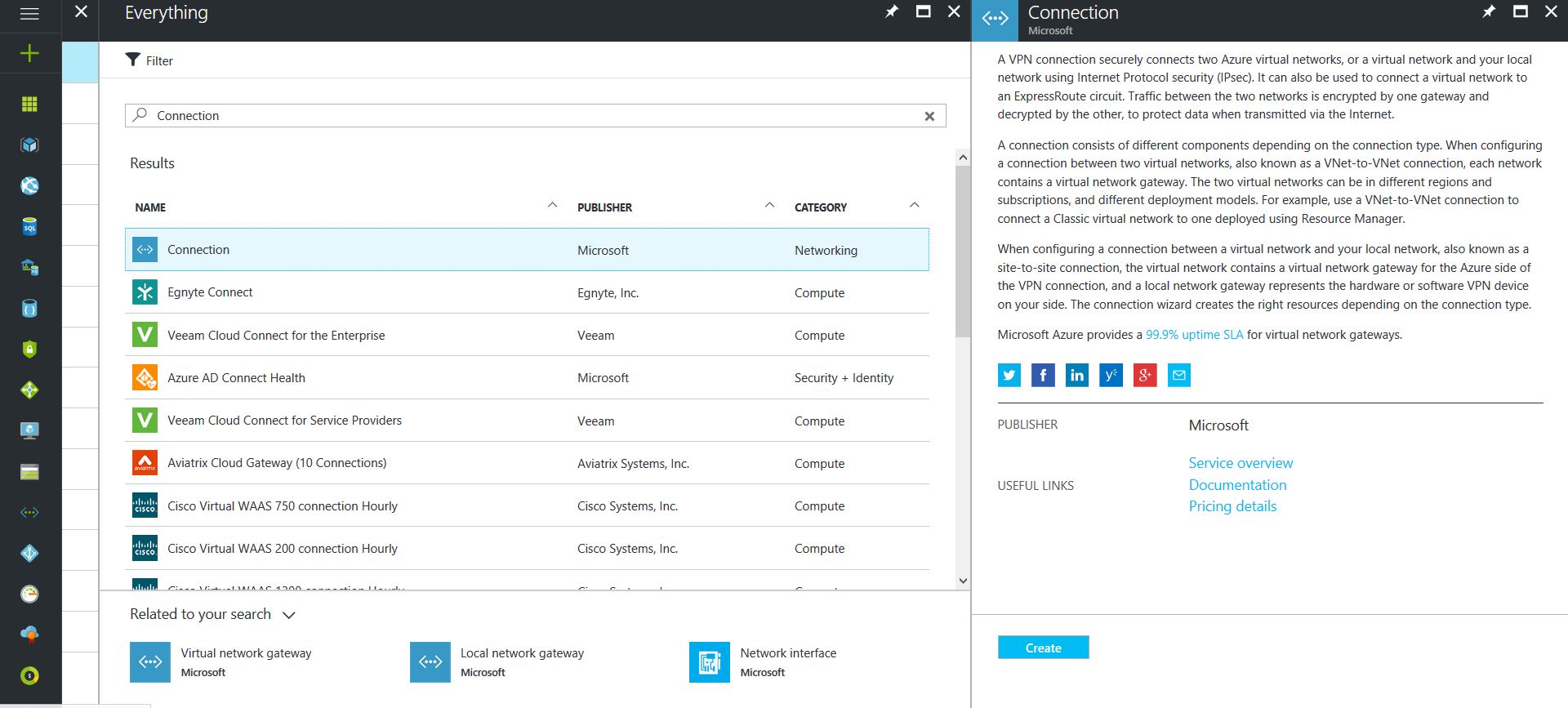
- Choose “Site-to-site (IPSec)” as the connection type
- Give the Connection a name
- Select matching Region to where Azure resources are located
- Leave the remaining values as their defaults and then click the “OK” button. On the summary screen click on the “OK” button to create the connection.
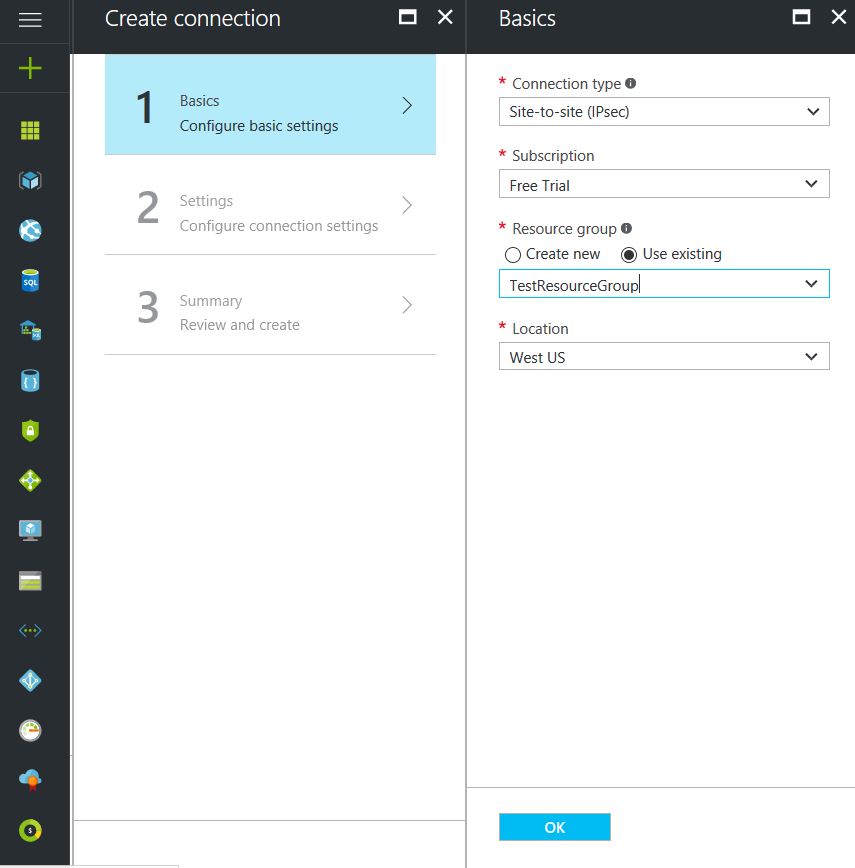
- Choose the newly created Virtual Network Gateway
- Choose the newly created Local Network Gateway
- Specify a shared key
- Leave the remaining values as their defaults and click the “Create” button.
This completes the setup of the Azure side of the VPN tunnel. Now to work on the Ubiquiti USG side.
Configuring an Ubiquiti USG VPN Network
This is a fairly simple process but it has to be precise:
- Choose the Current Site from the top right hand side of the portal.
- Click on the Settings gears down on the bottom left side of the portal.
- Click on Networks then on the “Create New Network” button.
- Give the connection a name, choose “Site-to-Site VPN” as the Purpose
- Choose “IPSec VPN” as the VPN Type
- Choose to Enable this Site-to-Site VPN
- Add the Azure subnet under Remote Subnets
- Get the newly created Virtual Network Gateway IP address from Azure for the Peer IP
- Enter the on-premise external IP address for Local WAN IP
- Enter the same shared key as used in the Azure VPN Connection for the Pre-Shared Key
- Choose “Azure Dynamic Routing” as the IPSec Profile
- Expand Advanced Options
- Leave Key Exchange Version, Encryption, Hash & DH Group as default and uncheck the PFS & Dynamic Routing boxes.
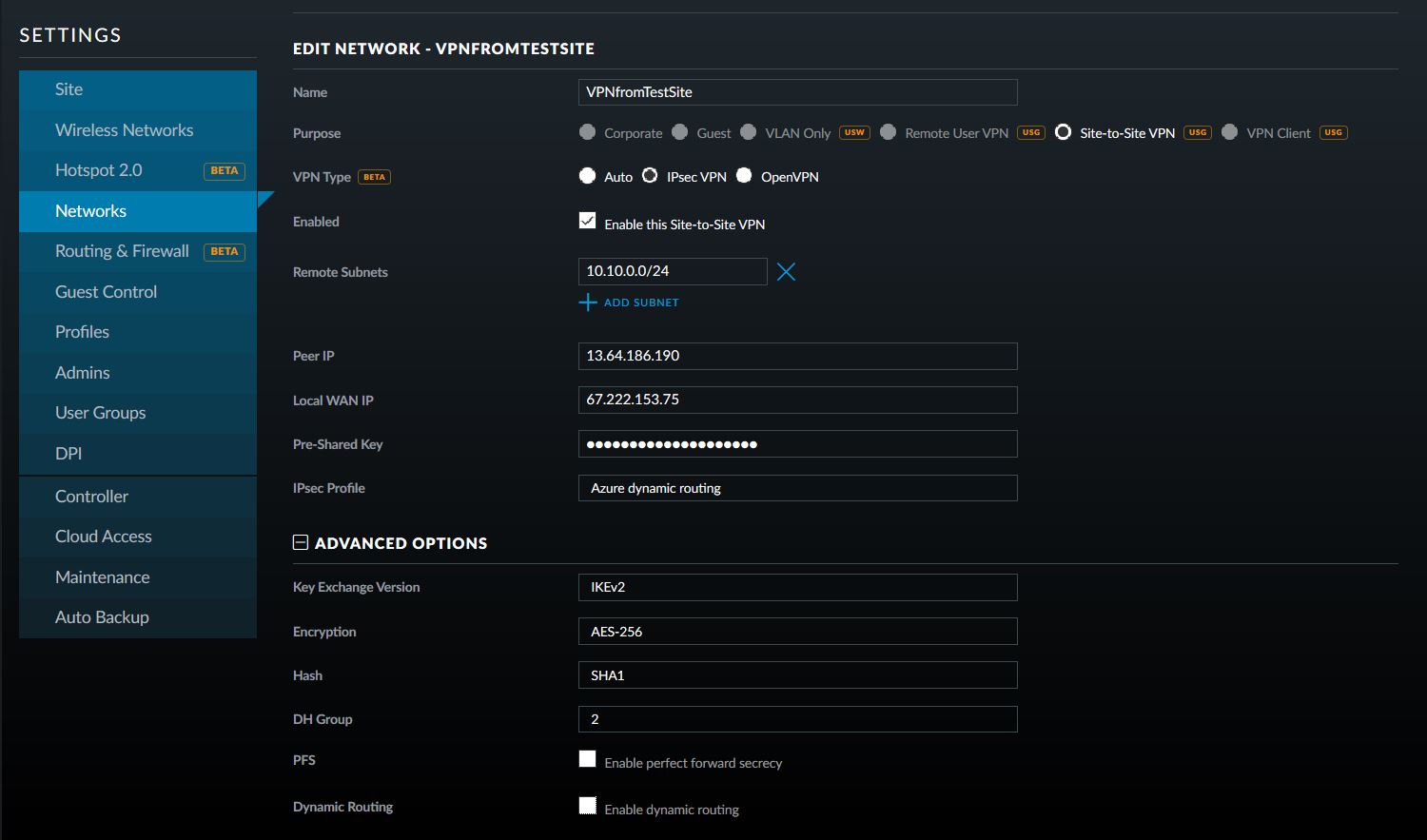
That is all there is to it. If you have any difficulties with connection then delete and re-create the Ubiquiti USG side first (those two check boxes at the bottom of the Advanced Options will check themselves again, but don’t be fooled by this quirk in the software). If your company is currently using either Microsoft Azure or Ubiquiti USG routers and would like a VPN created, then contact us for assistance.








Found a recent issue when troubleshooting this with a reader of this blog. If there are any other VPN connections setup behind the USG device and there are port forwarding rules for these, then the Azure site will not connect properly. Need to remove these rules then remove the Azure “Connection” and recreate it.
Just set this up with a USG Pro and connecting to Azure. Worked great the first time. Thanks for the great guide.
Glad to hear that this blog is helping someone.
Thanks for the guide! Helped me get setup.
Does anyone have any issues with the VPN dropping to Azure? I’ve setup DPD and its still disconnecting once every few days.
Hi, I followed this guide and it really helped, azure connected to my primary usg. However, I had a site to site vpn to another usg that had been working fine. That vpn has stopped working all together. Can you have two site to site vpn’s in harmony with Azure?
To connect multiple USG’s to a single Azure instance you will need to create a Route-based VPN. Look up your options here:
https://docs.microsoft.com/en-gb/azure/vpn-gateway/vpn-gateway-about-vpn-devices
IT looks like Ubiquiti has some good documentation on manually creating the route-based VPN here:
https://help.ubnt.com/hc/en-us/articles/115012305347
This will not work via the controller though. Any updates from the controller would wipe out the VPN coding.
I followed this step by step. I am getting the following error
Dropped due to Traffic Selector Mismatch
I’m assuming it’s my comcast business modem/router. I added my USG to the DMZ on the router but still cannot figure out why this is going on. Any advice?
I would check the modem / router to see if it has a BRIDGE mode that can be used instead. That will bypass any routing functionality and allow traffic directly through.
Thanks a lot for the detailed guide. I followed the steps, however on Azure side, the status is always indicating “connecting” and never reached “connected”
What could be the issue..?
Cheers
Troubleshot this with another tech recently, we found that the issue was with their Azure Address Space being a 10.0.0.0/24 subnet instead 10.0.0.0/16 subnet. We also then had to changed remote subnet on USG to Azure Gateway Subnet. That got the tunnel connected. Once connected we had to add the Primary Azure Subnet that contained the VMs they were trying to connect to on the USG remote subnet section.
Hello gents
Is it possible to add a second public IP in the same von gateway to assure a kind of High availability
Would have to be a secondary tunnel. Not thinking this is possible.
Thank you for guide. I came across the same problem that iTikoz had. Status is always “connecting”.
Did anyone find the source of this problem ?
Troubleshot this with another tech recently, we found that the issue was with their Azure Address Space being a 10.0.0.0/24 subnet instead 10.0.0.0/16 subnet. We also then had to changed remote subnet on USG to Azure Gateway Subnet. That got the tunnel connected. Once connected we had to add the Primary Azure Subnet that contained the VMs they were trying to connect to on the USG remote subnet section.
I followed your steps exactly and have been unable to get the VPN to work. Not sure whats going on and need assistance.
I would love the chance to troubleshoot this with someone. Feel free to call and we can work it out.
I also had the issue as others that the VPN was established, but trafic wasn’t going through.
What was needed to solve the problem was to enable dynamic routing on the USG (last checkbox at the bottom).
I have followed this and the Azure is showing as connected however I cannot get any traffic to flow. I try pinging to and from the Azure VM and cannot see it or the local machines. Any assistance that you could offer would be greatly appreciated.
Happy to help if you want to show me your config. Did you do the exact same everything that is in the post or did you modify anything?
I followed everything in the post plus
i tried a couple of things i saw you had added in the comments.
How do I attache files to send you here or should i use the support email.
I have followed the post except I gave them names that were more appropriate. I even used the IP addresses recommended. I just went over everything and I cannot see an error. How do I attach my config or do I email it to you at support@farmhousenetworking.com. Thanks
I have reread your comments and found that I needed to also add the 10.10.10.0/24 subnet to the USG and now I can ping the local network from the VM now but not the VM from the local network.
I feel rather stupid when I turned off the VM firewall I could ping the VM from the local network.
Glad you got it sorted.
Has anyone managed to get a USG to Azure S2S VPN working behind a cable router (virgin media) running in modem mode. I’m not getting a connection. It may be because of NAT I suspect so I tried the command “set vpn ipsec site-to-site peer authentication id “ to test but still no luck?
It is because of the modem being in “modem mode” and not in bridge mode. Data has to flow through to the Ubiquiti unaltered for the VPN handshake to occur successfully. The external IP address of the network has to be recognized as being on the Ubiquiti router.
Good morning! I am very new to working with Ubiquiti. In reading your post, do you have to modify the JSON file to get the VPN to work? If not, is it just adding the new VPN Site-to-Site network with the corresponding Azure info?
No fancy JSON editing to make the Ubiquiti USG to Azure VPN to work. Just make sure to follow the example. If you need help then let me know.
Any way to make this work with 2 wan connections and failover the vpn tunnel to azure?
Nope. Not with Azure. If both WAN were static IP addresses and you configured two different VPN connections to Azure, then… but the VPN tunnels are point to point, not point to multi-point. I would stick with the no answer here.
Great article. Q: I have three sites using USGs and I hope to join each to Azure over VPN for Active Directory authentication only. There will be no VMs in the cloud. Earlier in this thread, it was suggested that this would require route-base VPN. Can you confirm this is required for my purposes before I begin learning how to create route-based?
Thanks
It is route based. In this situation you would be creating three separate VPNs in Azure with separate subnets for each VPN tying into the network on Azure. If you need further help then feel free to send me an email.
As everyone states, great article. However, I must be a dummy, because I cannot get this working. Are you still offering help?
Always willing to help. I will email you.
HI, I have my USG sitting behind a BT ADSM router, which has my public address on it. So I’m confused as to what IPs I need to put into the local WAN IP. I think it needs to be the local IP (10.0.0.1 in my case) but then it gets NATed as it leaves the BT router. Do I need to put port forwarding on the BT router or is there any NAT traversal stuff I need to add? Any help is appreciated.
Need to change the BT ADSM router into bridge mode so that the USG gets the external IP address. NATing kills the VPN.